Automated Malware Analysis Using ANYRUN Sandbox
ANY.RUN is an automated malware analysis platform in which you can upload and execute any malicious file for analysis without any hassle.
Though Cuckoo Sandbox is among the preferred sandbox for many malware researchers. The only difference between the two is the ease of use and deployment. Moreover, the advanced features of ANY.RUN is paid while Cuckoo Sandbox is an open-source sandbox and that’s where it stands out.
So let’s start with the one simple malicious file I downloaded from the Hackersploit Malware Tutorials.
Note: Please don’t execute this file. Download and upload this to the ANYRUN console. Even if you wish to execute it for static file analysis, it is advisable to run it in a Virtual Machine with the “Host-Only Adapter” option under Network Settings.
Let’s begin, before accessing the ANYRUN platform, you have to register with an official email address. Once you completed the process and log in just Follow the following instructions:-
- Click on the New task option
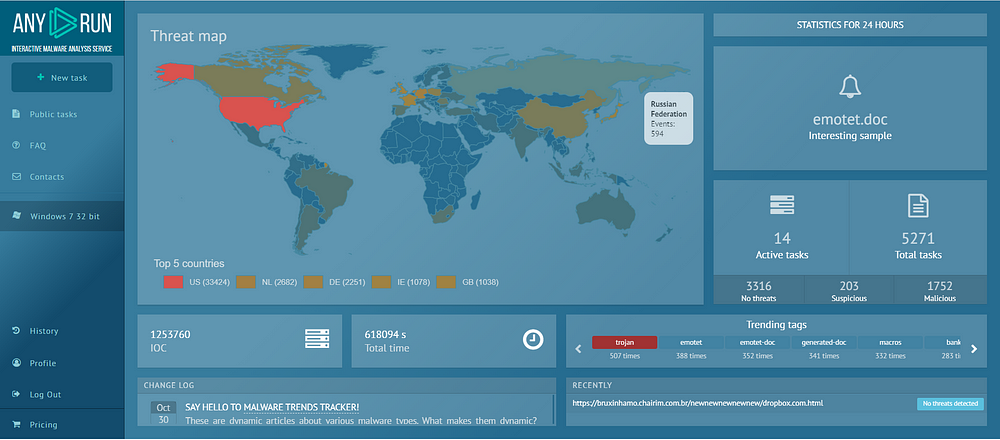
2. You can choose the Operating system inside which you want to execute your file. We can choose the URL as well for analysis.
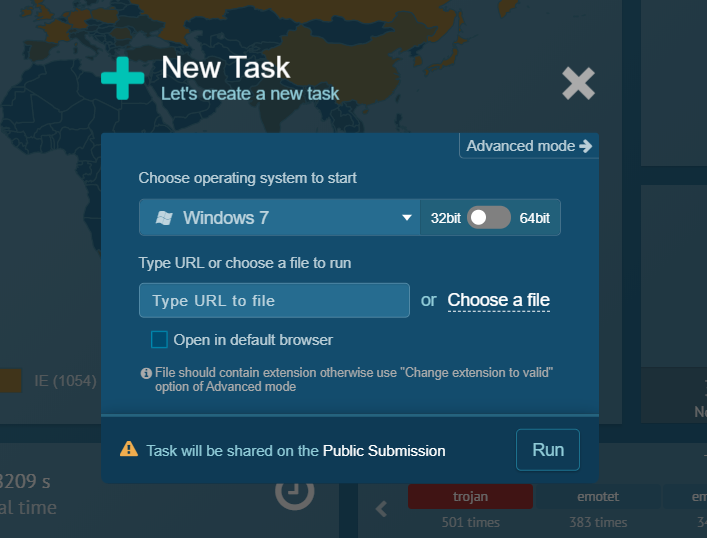
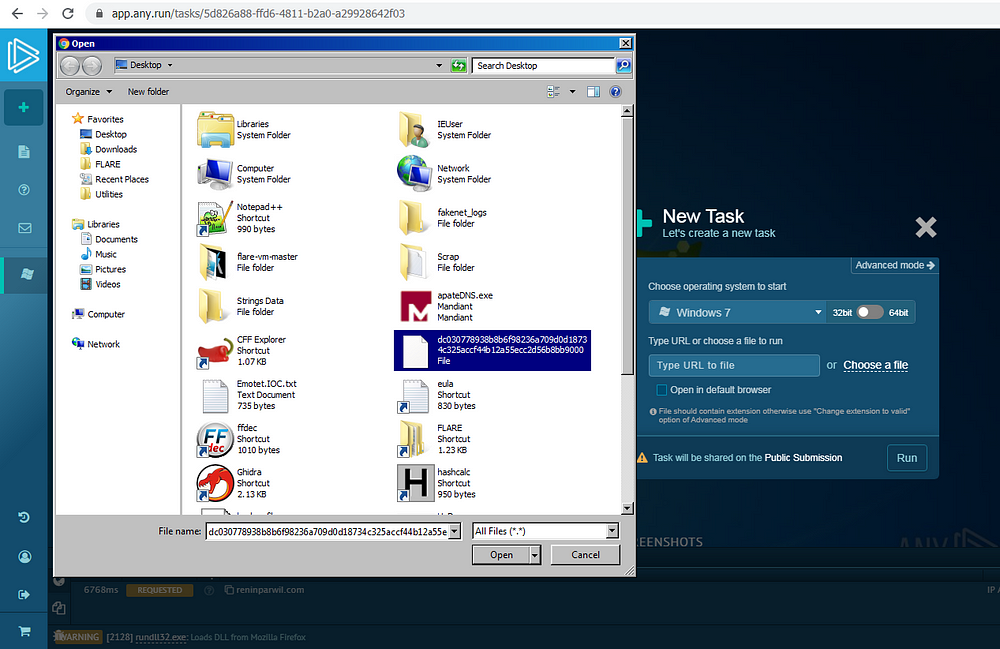
3. Now the actual malware is running inside the sandbox defined by you and after analysis, it will provide you much informative information that will help in further static file analysis.
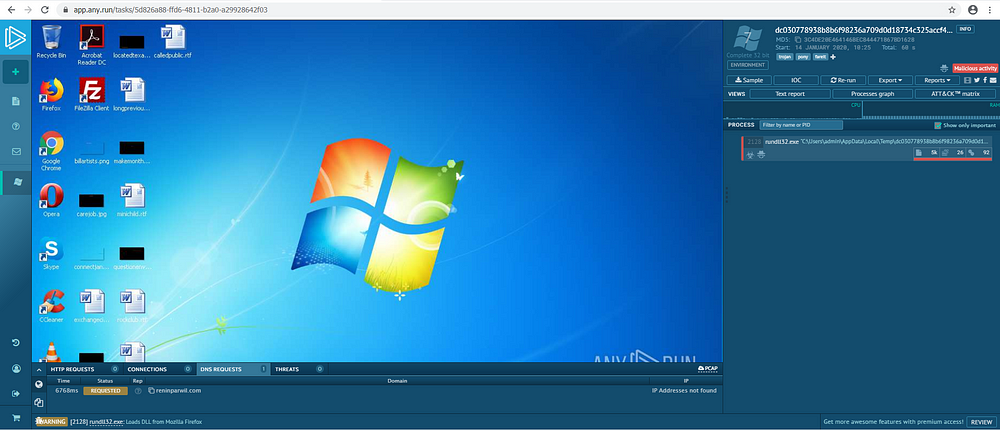
4. The key points are:-
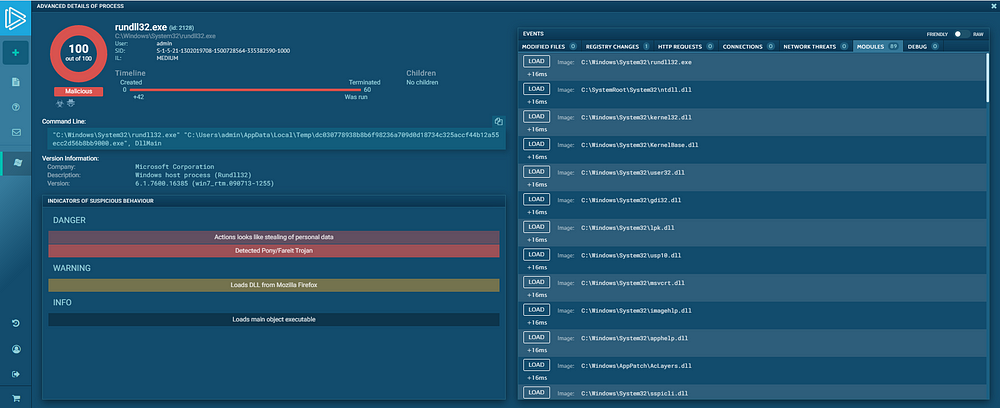
- PE File Identification (MX Header)- The file that we have uploaded is a malicious PE file with the name rundll32.exe and as per the ANYRUN database repository, it’s performing malicious activity.
Note: Some features are disabled for the free version. like Report feature where you can download the Virustotal report pertaining to the file we are analyzing (If Any)
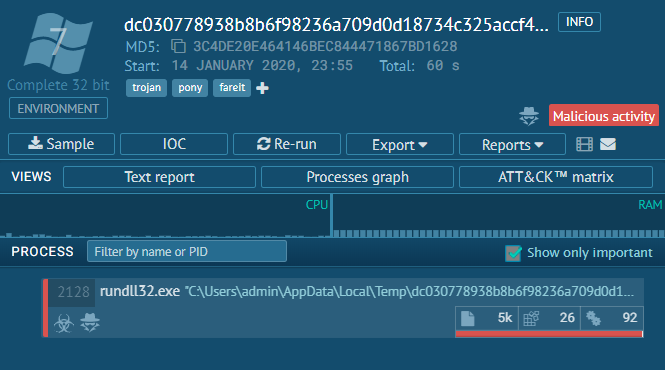
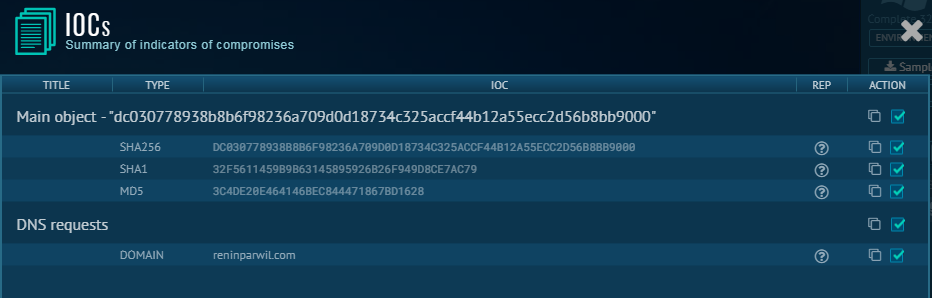
2. IOCs- The IOCs are the key parameters to look for. IOCs could be Hash, IP, Domain, Patterns, etc anything that can give us a hint about the malware and a threat associated. Here we can see the domain and hashes associated.
Note: Blocking IPs and creating signatures for hashes will not counter future threats as these parameters could be changed by adversaries. Therefore, detecting threats by the pattern is the key (Cyber Kill Chain and ATT&CK).
An efficient YARA rule with the patterns and conditions is advisable.
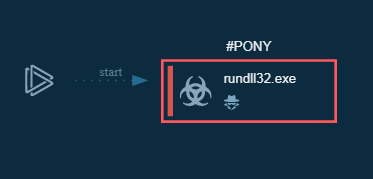
3. Process Graph- Since this file is short and doesn’t have dropper or fileless propagation etc. We couldn't able to leverage this feature as of now. But for complex malware, the process graph will help us in understanding the flow of the malware.
4. Static File Analysis- Modified file after the execution, Registry changes, HTTP requests, C&C connections, etc can be easily analyzed which will help us in manual static file analysis.
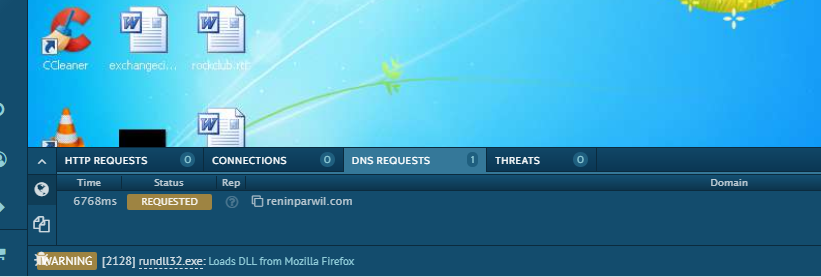
5. DNS Request- Instead of running your own Fake DNS and catching the DNS request, It will provide you a separate section depicting DNS request after the execution, In this example, malware is connecting to reninparwil.com domain.
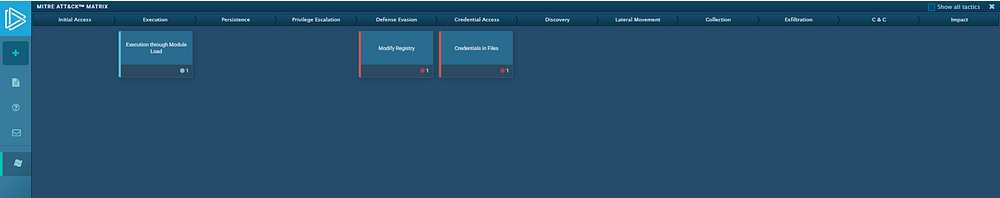
6. MITRE ATT&CK Matrix- We can visualize the malware activities in ATT&CK format for future threat detection playcards/playbooks. Moreover for the creation of robust YARA rules.
7. Custom Reports- From the Text Report option, we can download the summary report. A good report and detailed report.
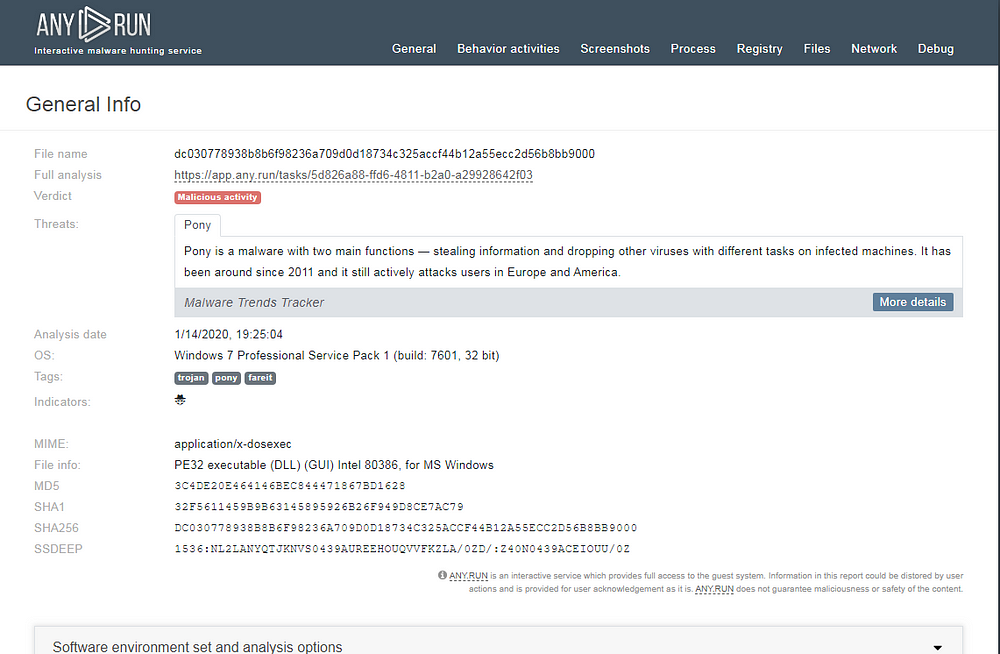
8. So what was that?
Pony Kind of Malware! :)
Thanks, and please provide your inputs and suggestions if I miss something.

Comments
Post a Comment