Urgent 11 Detection and Mitigations
Summary
The vulnerabilities are disclosed by the Armis research group via exploiting the VxWork’s TCP/IP stack (IPnet) implementations. For more information please visit the reference section. [1]
How would an attacker use Urgent 11?
An attacker may bypass the DMZ (i.e Firewall) via malformed/crafted TCP packets which could lead to the compromise of the industrial control appliances like PLC, SCADA, etc. This may also affect medical devices like MRI machines, patient monitors, etc. [2]
Note: Consequences of the Urgent 11 are many. However, we are considering only the industrial appliances. [1]
Detection and Mitigation
As a proactive threat hunter, it is advisable to build customized SNORT and Suricata rules pertaining to the Urgent 11. Also, validate the rules in NSM (Network Security Monitoring) platform.
In order to detect the vulnerability, we start with Nmap scan using -O switch. The following screenshots depict the Nmap scan against a single VxWorks-Based printer [3]:-
Nmap Scan for Urgent 11 Detection [3]
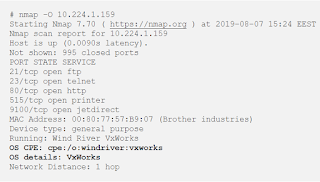
Nmap Scan with VxWorks OS Detection [3]
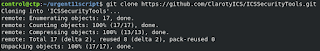
Also, we can use free python scripts published by Claroty to find the Urgent 11 vulnerabilities within the network. It can be easily installed by following below steps [4]:-
$git clone https://github.com/ClarotyICS/ICSSecurityTools.git
$sudo apt-get install python3 //Skip the step if python3 is already installed
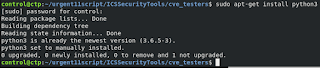
$pip3 install netaddr //Skip the step if netaddr is already installed
$pip3 install netifaces //Skip the step if netifaces is already installed
$pip3 install scapy //Skip the step if scapy framework is already installed
$python3 cve_2019_12258.py -h //Now we are ready to use the scripts
We can consider the following four points as a checklist for mitigation against the vulnerabilities. However, the first course of action is to disconnect all the affected systems and refrain using it:-
1. Build SNORT and Suricata custom rules.
Armis research lab has developed and introduced SNORT rules for firewall and IDS solutions to detect and prevent Urgent 11 vulnerabilities. All of them are listed below:-
#alert tcp any any -> any any (flags: U+; msg: “OS-VXWORKS — Use of Urgent Flag might indicate potential attempt to exploit an Urgent11 RCE vulnerability”; classtype:attempted-admin; reference:cve,2019–12255; reference:cve,2019–12260; reference:cve,2019–12261; reference:cve,2019–12263; reference:url,armis.com/urgent11; rev: 1; sid:1000002)
#alert tcp any any -> any any (flags: SUF+; msg: “OS-VXWORKS Illegal use of Urgent pointer — Potential attempt to exploit an Urgent11 RCE vulnerability”; classtype:attempted-admin; reference:cve,2019–12255; reference:cve,2019–12260; reference:cve,2019–12261; reference:cve,2019–12263; reference:url,armis.com/urgent11; rev: 1; sid:1000001)
#alert ip any any -> any any (ipopts: lsrr; msg: “OS-VXWORKS Use of LSRR option, potential attempt to exploit an Urgent11 RCE vulnerability”; reference:cve,2019–12256; classtype:attempted-admin; reference:url,armis.com/urgent11; rev: 1; sid:1000003)
#alert ip any any -> any any (ipopts: ssrr; msg: “OS-VXWORKS Use of SSRR option, potential attempt to exploit an Urgent11 RCE vulnerability”; reference:cve,2019–12256; classtype:attempted-admin; reference:url,armis.com/urgent11; rev: 1; sid:1000004)
2. Inject the rules into NSM (Network Security Monitoring) solutions.
How to validate the rules? The simple answer is Scapy
After validating the rules, add the rules into rules.conf file of the NSM platform and update it. (I would prefer using ELK with SNORT, Suricata and Yara).
3. Collect external TI feeds, Make a custom playbook (ATT&CK Framework, etc) and integrate it into your Threat Intelligence Platform/SIEM/SOAR (Anomali Threat Platform, LogRhythm, Splunk Phantom, etc)
This section is categorized into two parts namely Collecting Internal TI feeds and External TI feeds. The whole idea is to collect both the feeds and inject it into the Threat Intelligence Platform for detection. This way we can best prepare ourselves from undefined vulnerabilities and threats.
1. Collecting Internal TI feeds
Again my preference goes to ELK with SNORT, Suricata, and Yara- As these are Open Source tools.
If we are lucky enough to use the industry’s best tools then consider the plugins that were added pertaining to Urgent 11 in platforms like Kaspersky’s KICS, Tenable’s PVS (Passive Vulnerability Scanner), Claroty’s Continuous Threat Detection (CTD), etc.
The best practice is to use those plugins, make rules, and add value to NSM. If you are an internal threat hunter and an employee of the firm, the intelligence you are providing is internal TI feeds to your threat intelligence platform.
2. Collecting External TI feeds
There are many precise external TI providers pertaining to ICS/IACS like Dragos, US-CERT, etc. It is recommended to collect external TI feeds from those TI providers along with TTP, IOCs, etc and build a custom playbook for an attack. Furthermore, add these playbooks to your threat intelligence platform for further analysis and detection.
Collect External TI Feeds >> Build PlayCards/PlayBooks >> Integrate PlayCards into SIEM/SOAR/Threat Intel Platform >> Detect and Mitigate Attacks
Consider this one piece of advice in one sentence:-
“ Detect by patterns Not by IP, Focus on vectors, not domains”
4. Proactively look for OEM released patches.
Please provide your feedback. If any :)
References:-
[1] URL- https://armis.com/urgent11/
[2] URL- https://www.youtube.com/watch?v=bG6VDK_0RzU&feature=youtu.be
[3] URL- https://medium.com/sensorfleet/urgent-response-to-emerging-iot-vulnerabilities-with-open-source-tools-e5b72193670d
[4] URL- https://github.com/ClarotyICS/ICSSecurityTools/tree/master/cve_testers



Comments
Post a Comment